HomeBlog
Blog
Showing 1 - 10 of 28 results
Open Source Intelligence (OSINT) is a critical phase in cybersecurity that involves the process of gathering information about an organization...
-
-
November 5, 2023
The Cyber Kill Chain is a model used in cybersecurity to describe the various stages that adversaries go through during...
-
-
November 5, 2023
The Birth of Bitcoin (2008) Picture this: a mysterious figure, known only as Satoshi Nakamoto, registers the domain bitcoin.org. In...
-
-
October 17, 2023
In a concerning development, an AI chatbot named WormGPT has emerged as an alternative to ChatGPT, but with a dark...
-
-
July 16, 2023
Elon Musk, the visionary entrepreneur and CEO of Tesla and SpaceX, has announced the establishment of xAI, a new artificial...
-
-
July 13, 2023
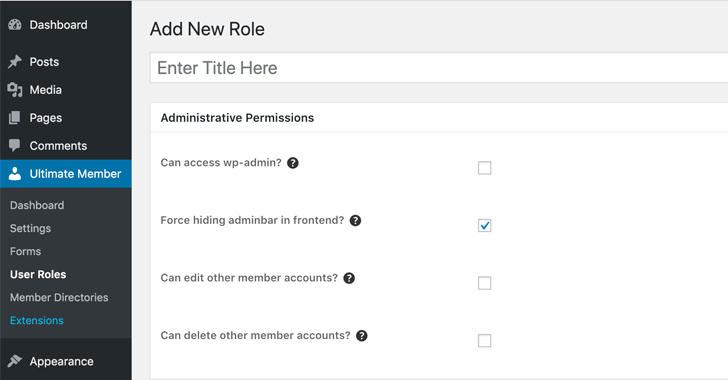
A critical unpatched vulnerability in the popular Ultimate Member WordPress plugin has been discovered, putting approximately 200,000 websites at risk...
-
-
July 2, 2023
A recent research study conducted by cybersecurity expert Chen Shiri has exposed a high risk security risk within Amazon Web...
-
-
June 27, 2023
Blockchain technology has emerged as one of the most transformative innovations of the digital age. Although it gained prominence with...
-
-
May 19, 2023
Microservices architecture has revolutionized the way we build and deploy software systems. With the ever-increasing demand for scalability and resilience,...
-
-
May 9, 2023
Containerization has revolutionized the way software is developed, deployed, and scaled. Docker, a leading containerization platform, offers a simple and...
-
-
May 9, 2023
Categories
🚀 Become a Microservices Expert!
Master microservices architecture, design scalable systems, and deploy with confidence. Learn hands-on with real-world projects and best practices.